Sensors | Free Full-Text | Code Injection Attacks in Wireless-Based Internet of Things (IoT): A Comprehensive Review and Practical Implementations

Hello cyberman!This article subject LDAP and hacking with LDAP. First of all, we need to know what LDAP is. The definition LDAP in Wikipeadia: The LDAP (The Lightweight Directory Access Protocol) is

The Gas Siphon Attack: The Technical and Economic Realities Behind Hacking Exchanges · Devcon Archive: Ethereum Developer Conference

Combating Information Manipulation: A Playbook for Elections and Beyond | International Republican Institute
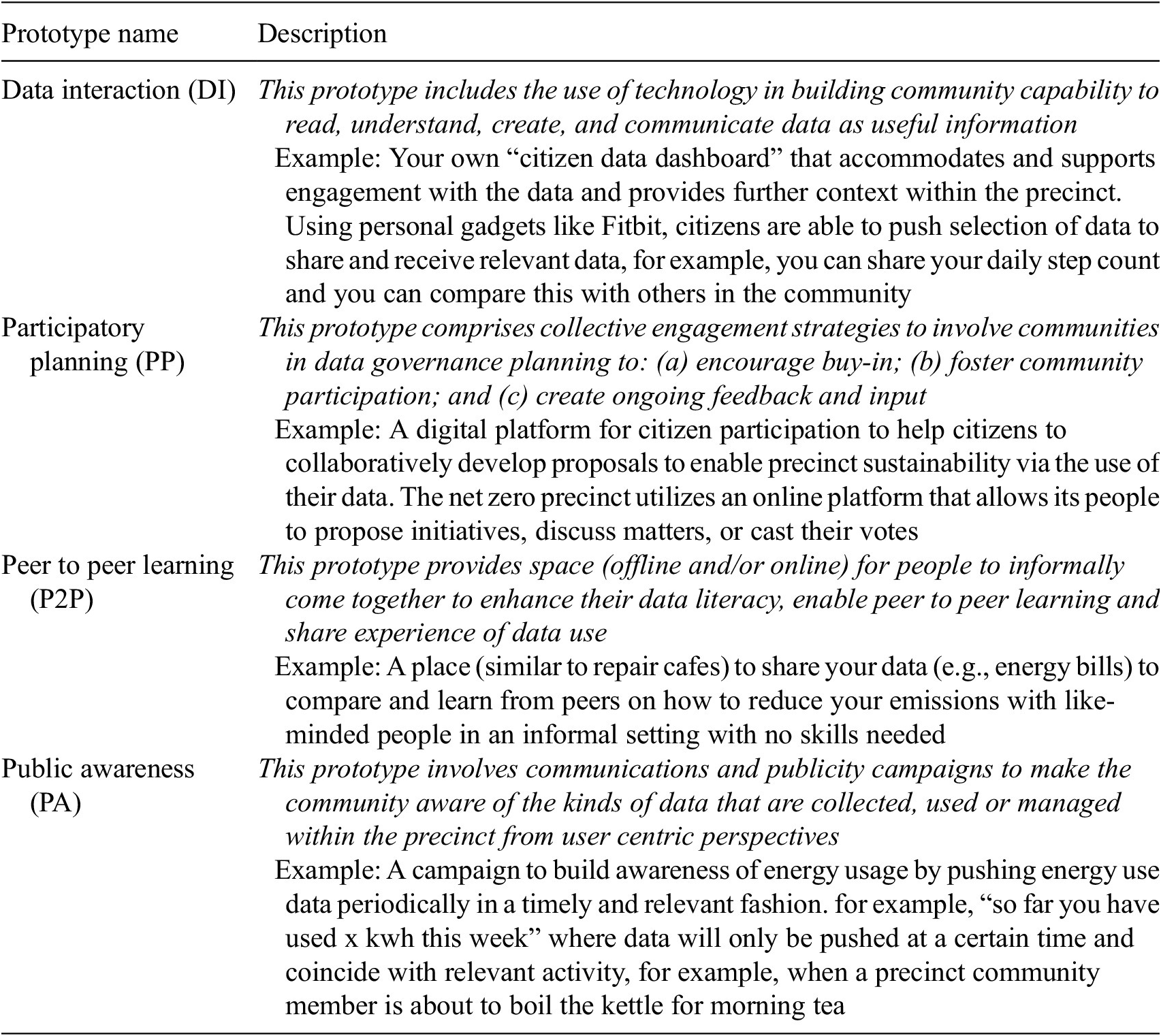
A participatory approach for empowering community engagement in data governance: The Monash Net Zero Precinct | Data & Policy | Cambridge Core




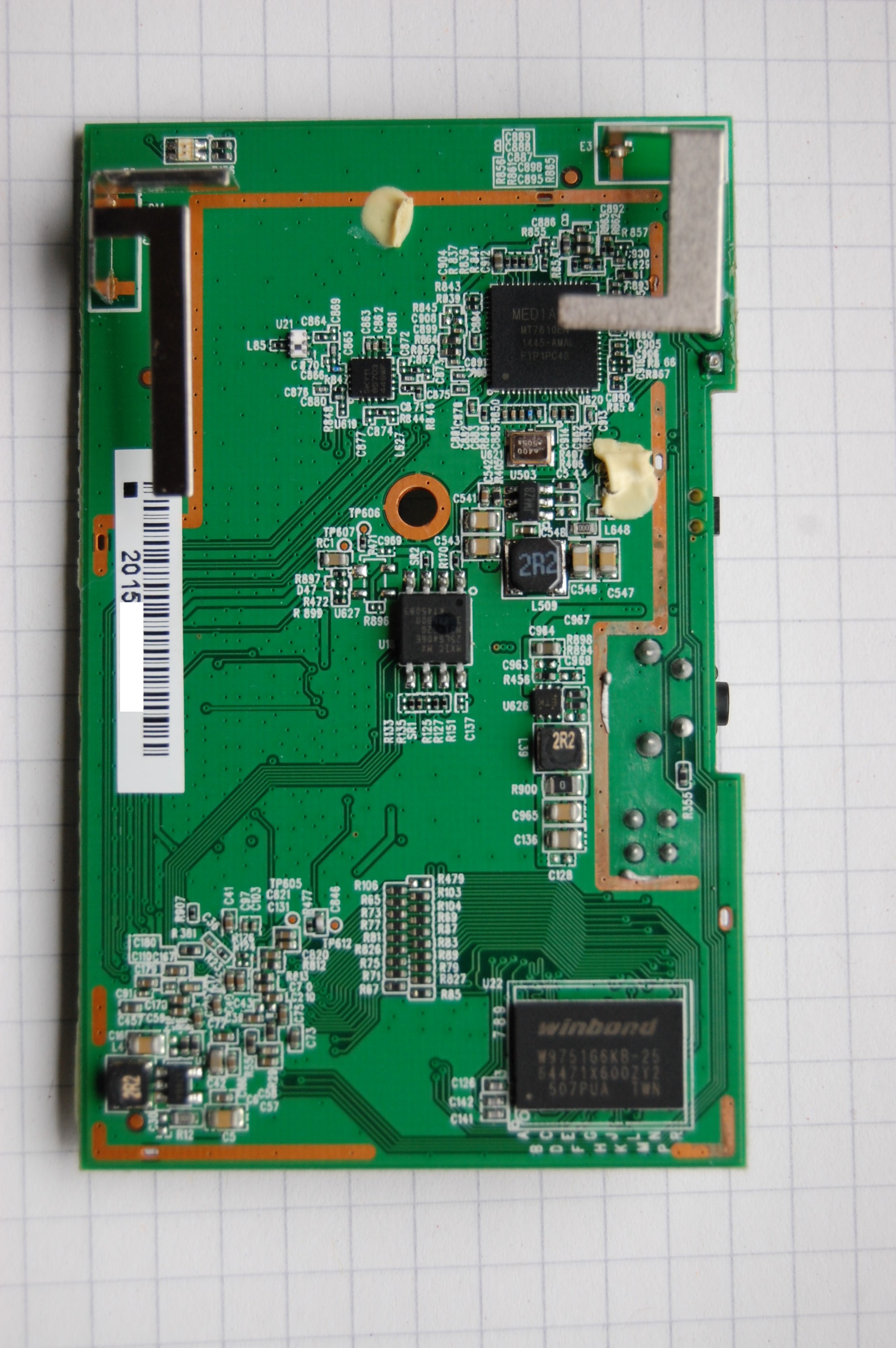
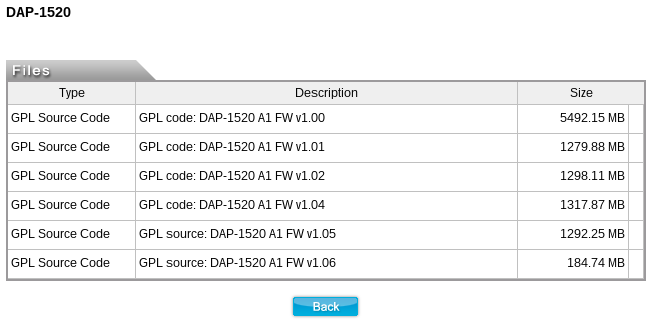
![Exploitation] D-Link DAP-1860 Vulnerability | by Infiniti Team | Medium Exploitation] D-Link DAP-1860 Vulnerability | by Infiniti Team | Medium](https://miro.medium.com/v2/resize:fit:1400/0*6Cs6yeRlMB6wIozc.png)

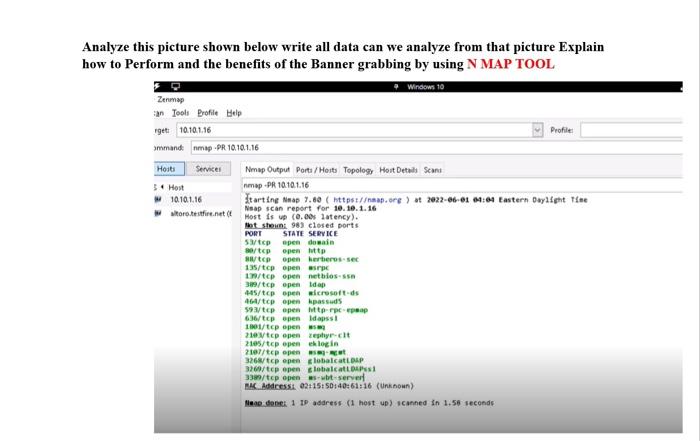

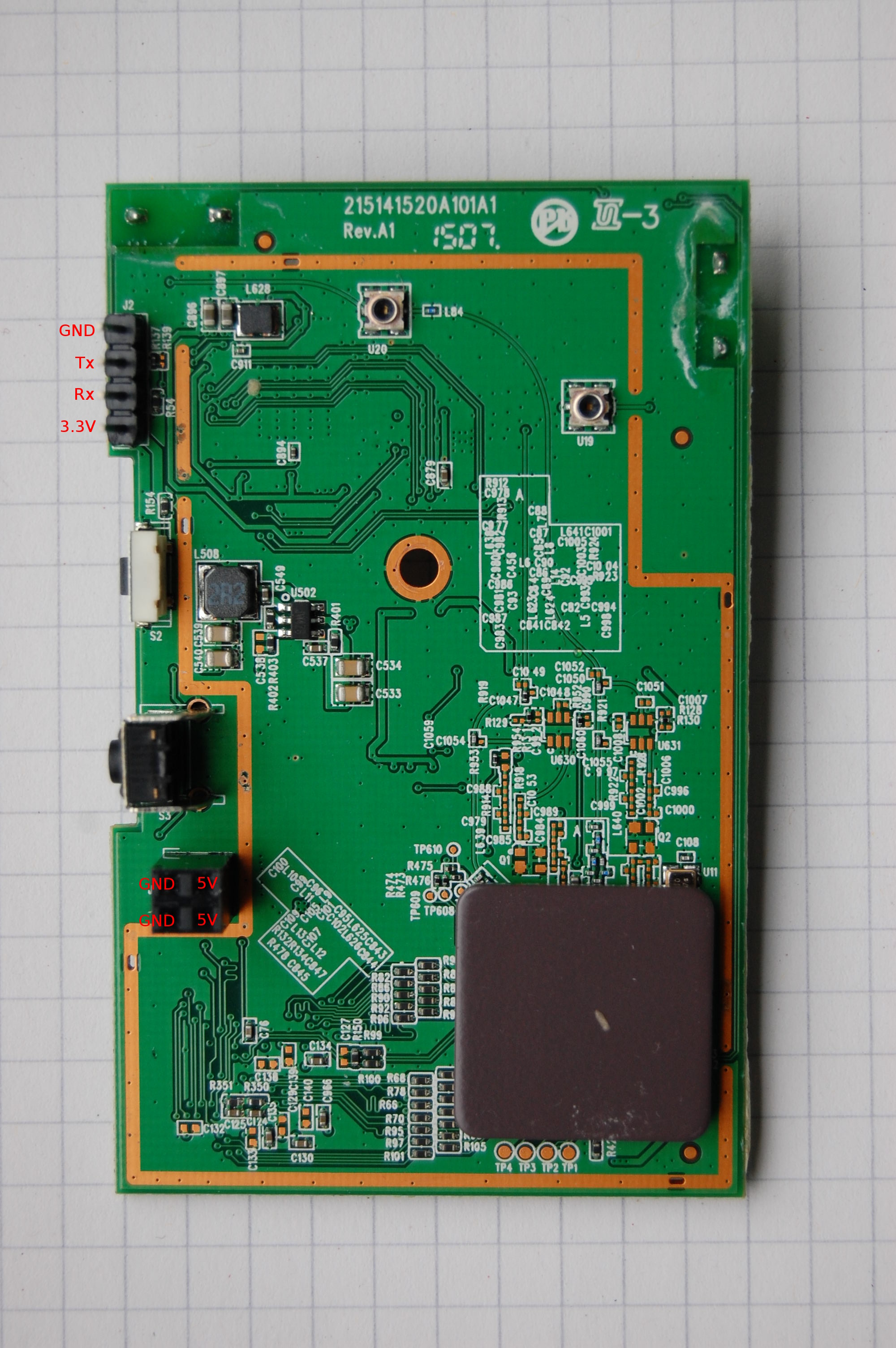

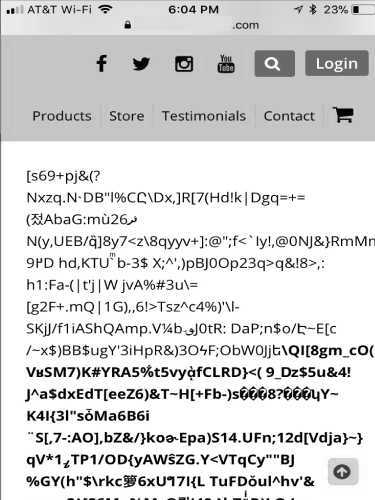
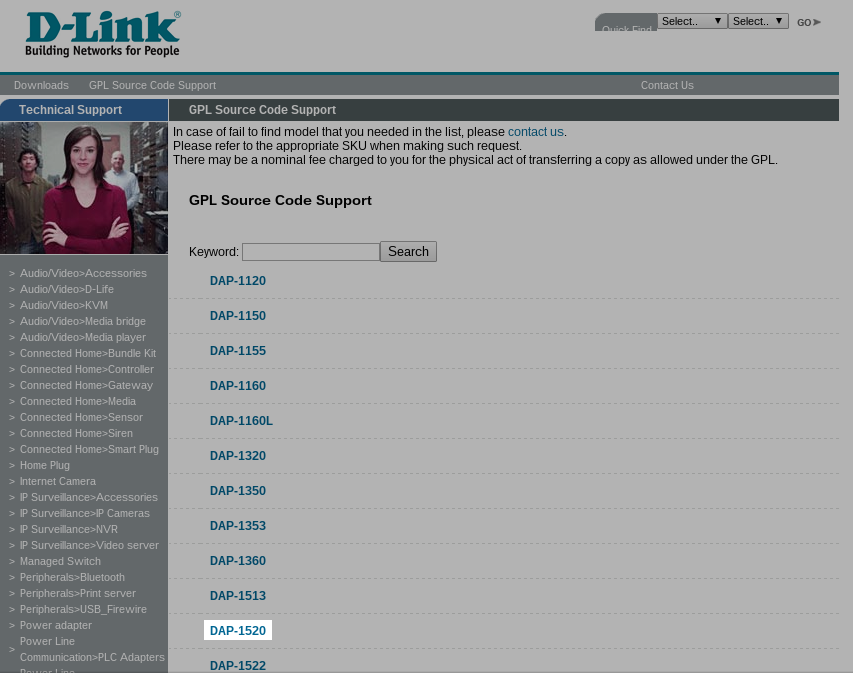


![Exploitation] D-Link DAP-1860 Vulnerability | by Infiniti Team | Medium Exploitation] D-Link DAP-1860 Vulnerability | by Infiniti Team | Medium](https://miro.medium.com/v2/resize:fit:988/0*R4W3w1UlpAdzrNbA.png)